Management Approach
Information Security & Cybersecurity Structure Committee
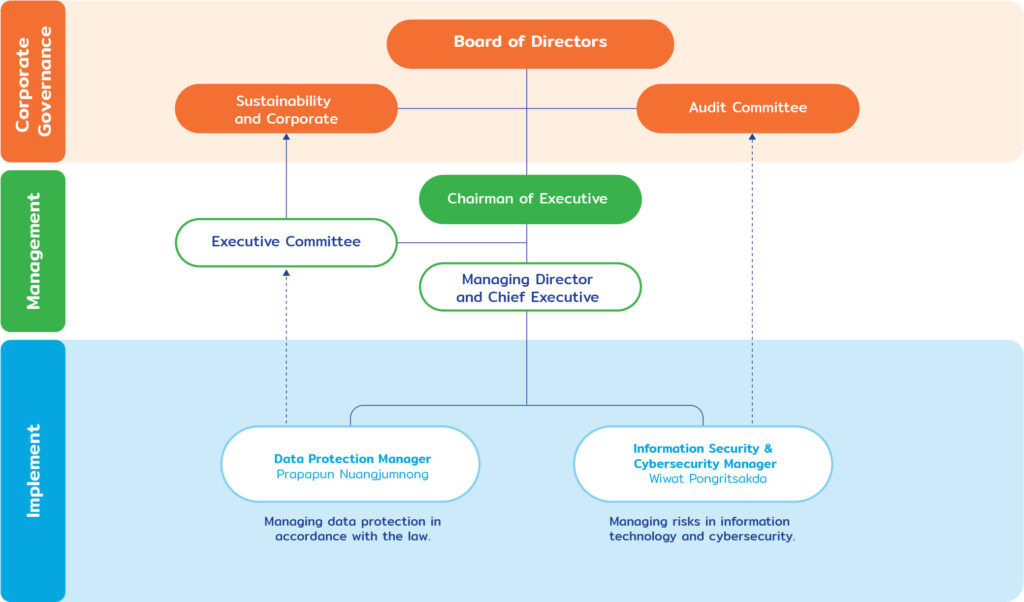
CP All Plc. and its subsidiaries (“the Company”) give importance to continuous development and strengthening of businesses, with the use of information technology and and cyber security technology. It is to increase effectiveness and efficiency of products and services, including internal work system improvements from the communication infrastructure both inside and outside organization, collecting and gathering data throughout the business chain, production and transportation planning, increasing productivity in factories, quality control of the production process, increasing the quality of service before and after the sale, maintenance, etc. Employees will have their own User Account in order to access the system and services of the organization according to the rights and necessities related to the operation and to ensure the use of information technology and cyber security. The organization has issued a policy regarding Information Technology Policy as a guideline for data usage, operations, development, and maintenance of information technology systems appropriately comply with laws and relevant security requirements for both employees, partners and customers The company has been certified to various international standards such as ISO/IEC 20000 for providing quality information technology services, ISO/IEC 27001 for managing secure information technology, ISO/IEC 27701 for managing personal data, and PCI/DSS V3.1 for payment data security, etc..
The Company has set up a management structure for integration from the center and business groups, with a central unit bearing and providing support the working groups consisting of the IT Governance Committee which is responsible for establishing policies and guidelines for the use of the monitoring system for information technology and cyber investment projects in the same direction and in accordance with business strategies.
Information Technology and Cyber Risk Management
The Company has adopted the risk management principles by having the risk monitoring committee and risk management team in managing information technology and cyber risk. In addition to assessing the risks from the Company’s activities, the Company also surveyed cyber threats of other organizations, both in the same and different industries, in order to learn and assess the potential risk that may occur to the organization and can also cause damage to customers, stakeholders, and business partners.
Cyber Security Management Goals
The Company is committed to developing and implementing information technology systems that are secure, maintain confidentiality, integrity, and availability of all information, and comply with important IT legal requirements, such as the Personal Data Protection Act B.E. 2562, etc., by operating with the following management principles and practices:
Principle
Cyber Security Management Measures of CP All Business Group
The company has adopted the NIST Cybersecurity Framework as a global cybersecurity framework and conducted risk assessments to lead to preventive, detective, response, remedial, and restorative measures to ensure that data and information are secure and ready for continuous service.

Identify

Protect

Detect

Respond

Recover
Personnel creating an organizational culture with safe cyber hygiene
The Company places great importance on building corporate culture and cyber threat awareness, dividing the target groups into 4 groups:
Giving importance and following up from top executives
Information and cyber security training and awareness raising
Motivating with clear rewards and punishments
Measurement improves measures and promotes a consistent safety culture
Cybersecurity Management Guidelines
The company has managed cyber security with the goals set out above. by setting important guidelines And it is carried out through both promoting personnel at all levels to have safe cyber hygiene. Evaluating and controlling important work systems to meet the specified safety standards. and operations are carried out by a team of system administrators, both preventive, surveillance, and deterrence using appropriate technology Compatible with business environments And cyber threats constantly changing
Cyber Hygiene Culture
Cyber Assurance

Cyber Operation
The above activities are carried out through the following personnel, processes and technologies:
People
Process
Technology
Policy
The Company manages cyber security under the information security policies and practice guidelines which enforce CP All Plc. and its subsidiaries including directors, executives, employees, and authorized third-party service providers to access information at each level of everyone’s confidentiality.
Process
The Company has established a unit for information and cyber security operations and management, with a Chief Security Officer and a Data Protection Officer directly responsible. Information system and information security services are certified to international standards.
As follows: ISO/IEC 20000 Information Technology Service Standard, ISO/IEC 27001 Information Security Management Standard, ISO/IEC27701 Personal Data Management Standard, and PCI/DSS V3.1 Payment Security Standard, etc.
Technology
The Company has invested in a computer center that meets international standards, including a backup computer center that is ready to work immediately and requires storing important customer data and information within the said computer center under the design of zoning and access control for authorized persons only. For managing cyber threat risks, the Company has installed appropriate technologies to prevent, detect, stop, and alert as follows: Firewall, Intrusion Prevention System, Anti-Malware, Web & Mail Security, Threats Detect & Prevention System, Active Directory, Two-Factor Authentication, Privileged Access. Management, Patch Management, Security Information and Event Management (SIEM), including the making of Vulnerability Assessment and Penetration Testing in critical systems, either before services or when significant changes occur and in annually.
Personnel
There are trainings and testing to raise awareness and beware of Cyber Attack through Cyber Security Awareness and Cyber Drill for employees and executives at all levels. The Company also attaches importance to the security operation team by supporting and promoting training, testing to pass international standards certifications such as CISSP, CISA, CDPSE, C|HE (Certified Ethical Hacker) CompTIA Security+, as well as having a group of cyber practitioners, experts for advising, and business partners from both domestic and international that are engaged in working and overseeing related technical systems.
Cybersecurity Management Performance Results for 2023
| Topic | Target | Number of target groups | Percentage |
|---|---|---|---|
| Cybersecurity Awareness Training | Store Employee, Office | 94,934 Persons | 100% |
| Cybersecurity Engineer Training | Security Administrator | 31 Persons | 100% |
| Cyber Drill Test | Office | 14,484 Persons | 100% |
| Incident Response Plan drill | Executive | CMC, BIRT, CSIRT Team | 100% |
| Topic | Industry average | Score |
|---|---|---|
| Cybersecurity Self-Assessment By CPG | 88% | 89% |
| Cybersecurity Resilience Survey By SET | 2.01 (1.0 – 5.0) | 4.43 |
| Security Rating By BitSight Service | 730 (100 – 900) | 800 |
The Company has conducted a cyber risk assessment based on the NIST Framework and has taken action to enhance its outstanding cyber security in 2023 as follows:
| No. | Process | Outstanding Information Security and Cyber Security Projects in 2023 |
|---|---|---|
| 1 | Identify | The Company assessed its IT security system against international standards (Cybersecurity Gap Analysis) according to NIST standards in 2023. The assessment results are summarized as the following main issues:
|
| 2 | Protect | The company has improved the process of accessing important systems by introducing the technology of personal authentication (Privilege Assessment Management & 2FA) and encryption at the user level (Disk Encryption) to increase security, reduce the risk of data theft and comply with the enforcement of the Personal Data Protection Act B.E. 2562 by operating as follows:
|
| 3 | Detect | The company has taken steps to upgrade the Cyber Security Monitoring Center (Security Operation Center) by improving surveillance, storage, and analysis of security breach events. that works on centralized technology And there is a team to keep watch all the time |
| 4 | Respond | The company is continuously preparing for unusual situations by conducting drills to simulate attacks on major IT systems, ransomware attacks, and personal data breaches, as well as testing employees on how to respond to phishing emails (Phishing Simulations Test) |
| 5 | Recover | The company arranges data recovery testing for the Backup & Recovery system 2 times a year and is able to recover according to the target |
Related Policy and Guideline
| Information Security Policy | Download |
